In recent years, almost no topic has occupied the minds of IT security experts as much as that of the zero trust model. It’s true that its effect is huge, because its implementation means traditional perimeters become obsolete. So what’s behind the hype?
Nowadays, firewalls are standard equipment for securing company networks. They stop external digital attackers from accessing internal resources, stealing data or introducing malware. But what happens if a hacker gets past the firewall? Then it’s pretty easy for them to access internal resources and systems.
An additional complication is that most companies are increasingly moving their business applications into the cloud and many of their employees are now working from home. This means they are beyond the protected perimeter and must access external applications. What’s more, they often use all kinds of end devices which are generally not all from (or approved by) their own IT department.
Changed realities in corporations
The traditional perimeter model still works very well if all the employees are situated within the company’s secured structures – and only access the resources located within these structures. But today’s reality is generally somewhat different. The perimeter is no longer just at the edge of the network. It is wherever the company’s employees are.
According to a study by the security company Proofpoint and observeIT, the risk due to insiders has also increased in recent years. Between 2018 and 2020, the number of security incidents triggered by insider threats grew by around 47%. Cases of identity theft tripled during this period. In many companies, an attacker who suceeds in acquiring certain login data can use it to access all the resources linked to that account.
Is the situation hopeless? Certainly not. Zero trust is one model able to solve these problems. It was developed and introduced by Forrester more than 10 years ago. Google has also played an important part in the model’s increased popularity in recent years. The internet giant has been using it with great success for a while now. Nowadays the company is even selling its experiences under the brand name BeyondCorp.
More than just a piece of software
But zero trust is far more than just some software which you can buy and install. To be truly effective, zero trust needs to be a way of thinking – implemented throughout the company. The model assumes that, to start with, absolutely no one can be trusted – not even the CEO or the system administrator. Hence the name “zero trust”.
In the zero trust model, every user, every device, every service and every piece of communication are, initially, not trustworthy. Their attempts to connect are blocked as standard. Unlike traditional perimeters, it doesn’t matter whether the resource is located inside or outside the company network.
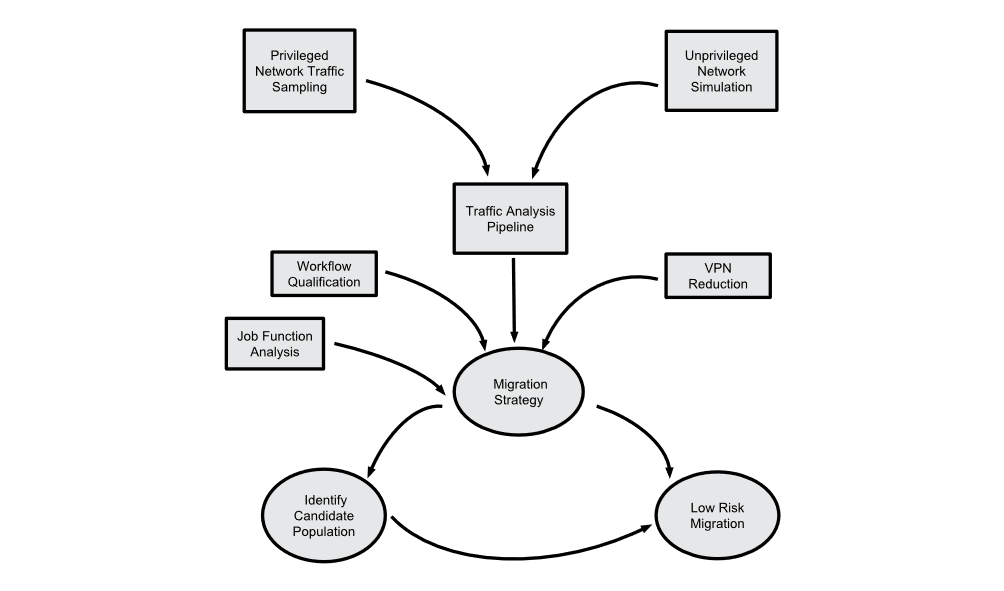
Migration to a zero trust model is a complex process.
Source: BeyondCorp.
When a user wishes to access a resource, their request is initially blocked. First it must be checked and authenticated. Even when access is subsequently granted, it is limited to the absolute minimum amount necessary. This approach is known as segmentation, or using micro perimeters, which split the company network into smaller structures. These are easier to separate from each other and are therefore easier to control. However, this doesn’t make the administration any easier. So once they have penetrated the network, a hacker is restricted to the compromised part of that network, and can no longer move laterally within the network to infiltrate other systems. A zero trust platform controls in detail who is permitted to access what, where and when in the network.
Getting started with zero trust
But that means a company must first know about all the devices, applications and resources it has. Each of these devices and services represents a potential risk. The company also needs to know how employees do their work: which applications they use and which resources they need to access. It’s complicated, but not rocket science. In fact, small companies generally find it easier to implement zero trust models than larger companies. This is partly because their systems are generally not so tightly interwoven. All the same, getting started with the zero trust model involves a certain amount of effort, because the entire company needs to get behind it. It isn’t just a technical change which needs to happen, but a change to the whole corporate culture.
If you have questions about the zero trust model and its implementation in practice, then please get in touch with us. We’d be delighted to provide you with technical support and advice.

Questions?Just ask!
I am Paul Pietsch from the HCD sales team. I will be happy to advise you or assist you with any questions. You can phone me on +41 58 590 110-0 or reach me using our contact form.
Contact us